
2018-11-01 UPDATE:
I did want to clarify in clear terms a handful of inaccurate claims I have seen made regarding this report.
- This was not a hack. Full stop. I've seen zero evidence to indicate this data was leaked as a result of any kind of compromise or "hack". Claims of that nature are simply inaccurate.
- I have seen claims that this was related to Flutterwave, but I have seen no evidence that Flutterwave was involved or compromised in any way.
- The data is no longer being leaked or at risk. The S3 bucket has been secured, and I have securely deleted the data that was used in the analysis of this report.
Summary
In the normal course of scanning for open/exposed/vulnerable Amazon S3 buckets I discovered a bucket containing a large number of CSV files. This is not all that odd. What made this bucket particularly interesting was that following a brief investigation it became immediately apparent the bucket appeared to be owned by an airline or a payment processor for an airline. After a thorough review of the files, I concluded these sensitive files were very likely owned by Arik Air. I had not heard of Arik Air, but they describe themselves as "West-Africa's leading airline" source. Arik Air has had a number of financial troubles which most recently lead to the Nigerian government needing to takeover of the airline to prevent it going backrupt. source Long story short -- this seemed like a potentially important find.
After concluding the CSV files were very likely owned by Arik Air (or their payment processor) I immediately attempted to make contact with Arik Air to notify them of this data leak. To say this process was challenging would be an understatement. I can confirm roughly 1 month after notice was provided that action has finally been taken to secure the S3 bucket.
Notification and remediation:
I attempted to notify Arik Air via social media, all of which failed (at least initially). I attempted to email [email protected] (which bounced) and the email address they publish on their website [email protected] -- which received no reply. After multiple messages on their coporate Facebook page and Facebook messages I eventually received a reply and they provided me with the email address for a security point of contact. Several days later the security point of contact confirmed they would review my report, and that was the last I heard from Arik Air. In all -- roughly 1 month elapsed from the time I notified them to the time they took action to acknowledge my report and to secure their customer's data.
Incident Timeline:
| Date | Event |
|---|---|
| September 6, 2018 | open bucket discovered. |
| September 6, 2018 | attempt made to notify. No Twitter account, message left on Facebook page, message sent via Facebook. No replies to any of these attempts. |
| Septmber 7, 2018 | message sent to Arik Air employees on LinkedIn. |
| September 10, 2018 | [email protected] and [email protected] notified via email. The security@ email bounces. |
| September 17, 2018 | Message on Facebook finally replied to. |
| September 18, 2018 | email provided for a security point of contact. No Reply. |
| September 23, 2018 | another email sent to the security point of contact. |
| September 24, 2018 | security point of contact replies indicating "it's been reviewed". |
| October 10, 2018 | No further reply received, but bucket has been properly secured at some point following Sept 24 email. |
What's in the bucket:
So what's in the bucket? That's the question and answer you came to find out.
The answer -- 994 CSV files. Some of these CSV files contain in excess of 80,000+ rows of data while other files contain 46,000+ rows of data, and in some cases files only contain 3 rows of data.
Here's a sampling of the data points that were leaked:
- Customer email address
- Customer name
- Customer's IP at time of purchase
- A hash of the customer's credit card
- What appears to be last 4 digits of the credit card used.
- What appears to be maybe be the first 6 digits of the credit card used.
- A unique device fingerprint (presumably the user's mobile or desktop device?)
- Type of currency used
- Payment card type
- Business name related to the purchase (more on this below)
- Amount of purchase
- Date of purchase
- Country of origin of the purchaser
- Charge message (chargemessage) associated with the purchase (more on this below)
- The "sector" field was populated in some cases. This appears to include the specific departing airport and arriving airport (more on this below)
High level stats
| Stats | Count |
|---|---|
| Number of files inthe bucket | 994 CSV files |
| Date range of leaked data | "2017-12-31T02:25:59.000Z" - "2018-03-16T14:08:50.000Z"(Roughly 3.5 months of data.) |
| unique devicefingerprint | 41,304 |
| unique pcardl4 | 9,989 |
| unique pcard6 | 3,517 |
| unique pcardhash | 71,065 |
| unique IPs | 35,593 |
| unique emails | 65,412 |
| unique customer names | 54,011 |
Regarding the "business name" field:
It's not entirely clear who the owner of this data is as Arik Air didn't reply with any further clarification or details. That being said it certainly seems likely to be a bucket controlled by Arik Air, or one of their immediate partners/processors. The fact that all of these purchases have an "acctparentbusinessname" value leads me to believe this could be a payment processor specific to businesses and/or travel agents. It seems unlikely a business name would be populated for personal travel conducted by an individual. In many cases the email address associated with a user also appears to be a travel agent or company email address.
Regarding the "charge message" field:
This field appears to be additional information associated with the attempted purchase. What makes this field particularly concerning in the context of the other leaked data is that it contains information regarding the 2 factor authentication (2FA) at the time of purchase. It references a partially obscured phone # or email address (or both) where the 2FA code is being sent.

A malicious person could potentially use this sensitive information to then target one of these customers of Arik Air for identify theft. With the information included in this leak a fraudster would have plenty of useful data points -- the person's name, email, first 6 and last 4 of the credit card, and a hint as to what the person's 2FA values might be so they could then focus on compromising that 2FA account (email or phone number) to take steal the user's identify.
Regarding the "sector" field:
In some cases this "sector" field is populated. Using this value in combination with a customer's email address it is possible to map out all flights this user has taken in the 3.5 months contained by this leaked data.
When pivoting on a single customer's email address we see the following pattern of travel:
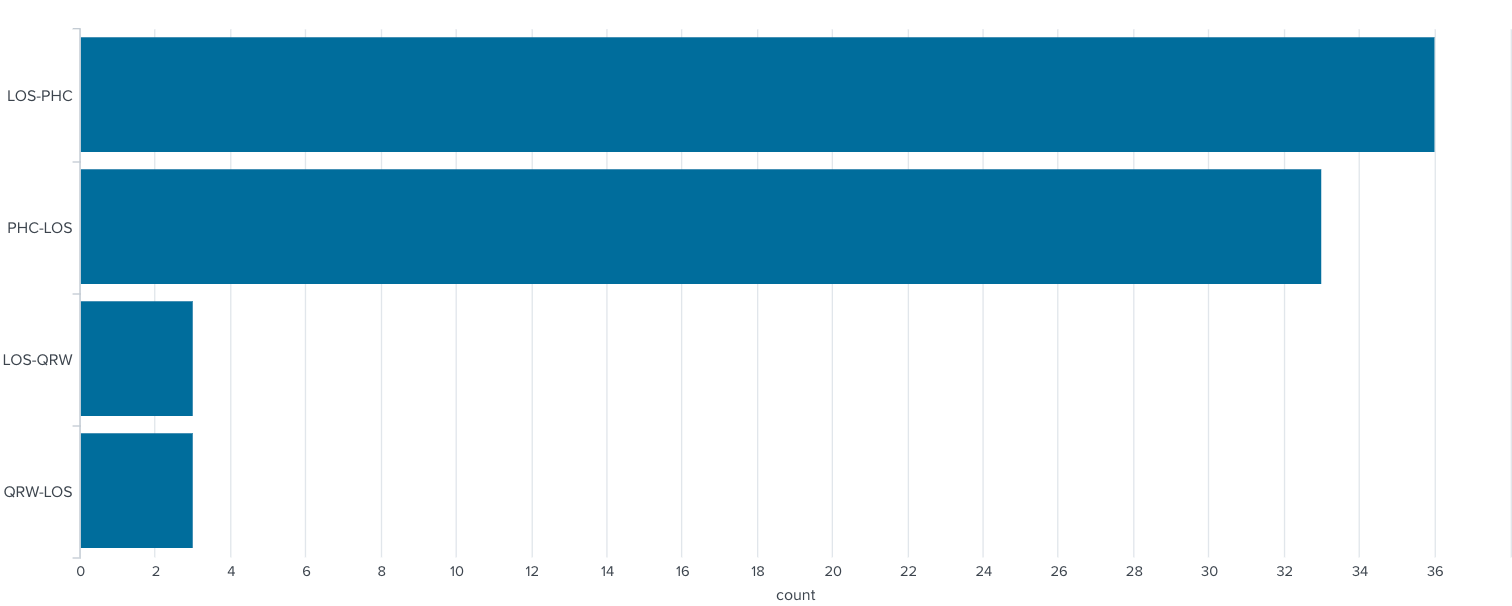
One might certainly consider this to be sensitive information in combination with the customer's name, date of flights, travel itineary, and what looks to be the first 6 and last 4 digits of the customer's credit card number.
Overall travel patterns from this dataset are as follows:
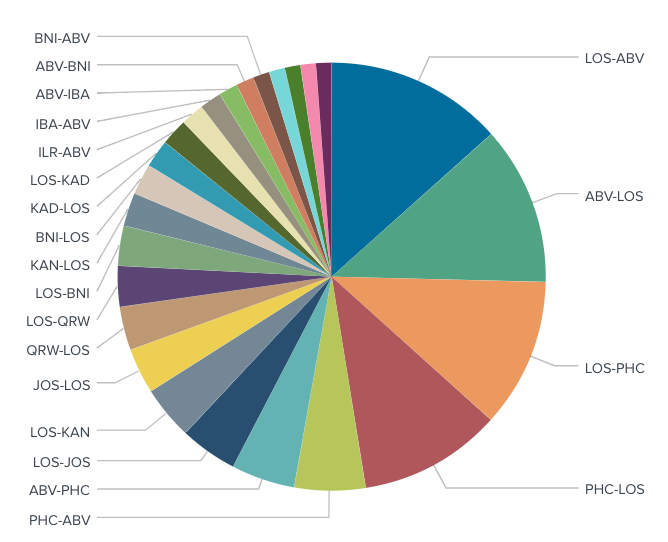
Other stats
Information below is in the format:
Friendly name (fieldname)
Customer Email (custemailprovider)
| Customer Email Provider | Count |
|---|---|
| GMAIL | 301376 |
| YAHOO | 203951 |
| COMPANY EMAIL | 81648 |
| YAHOO UK | 17036 |
| HOTMAIL | 11683 |
| MICROSOFT | 4715 |
| YAHOO MAIL | 3673 |
| AOL | 1655 |
| APPLE MAIL | 920 |
| YAHOO INDIA | 529 |
| YAHOO BRAZIL | 126 |
| YAHOO GERMANY | 100 |
| ZOHO | 79 |
| BT UK | 37 |
| YAHOO MEXICO | 30 |
| YANDEX RUSSIA | 9 |
| COMCAST | 6 |
currency (currency)
| Type of Currency | Count |
|---|---|
| NGN | 590611 |
| USD | 12105 |
| KES | 10368 |
| EUR | 7848 |
| GBP | 4512 |
| GHS | 2096 |
| ZAR | 39 |
Account business name (acctparentbusinessname)
| Account Business Name | Count |
|---|---|
| Teflon Hub | 268490 |
| PayportSA | 20736 |
| Fidelity Bank | 2625 |
| Access Bank | 2332 |
| Sterling Bank | 1588 |
| Access Bank Ghana Plc | 760 |
| Union Bank PLC | 272 |
| PayByana | 210 |
| Gene Solutions Multiservices Company | 68 |
| Brinq Africa | 60 |
| Crenet TechLabs Limited | 34 |
| Flutterwave | 22 |
| NTEL | 5 |
Account country (acctcountry)
| Account Country | Count |
|---|---|
| NG | 583059 |
| CA | 22386 |
| CY | 17738 |
| NL | 3070 |
| GH | 805 |
| GB | 242 |
| SE | 236 |
| ZA | 17 |
| BG | 11 |
| IN | 8 |
| 1 | 6 |
| US | 1 |
Payment type (paymenttype)
| Payment Type | Count |
|---|---|
| card | 570224 |
| account | 32861 |
| cpos-terminal | 11457 |
| mpesa | 10235 |
| ussd | 935 |
| mobilemoneygh | 882 |
| mcash-offline | 636 |
| paypal | 188 |
| account-internet-banking | 82 |
| account-ach-us | 73 |
Payment card type (pcardtype)
| Card Type | Count |
|---|---|
| MASTERCARD | 437457 |
| VISA | 97713 |
| VERVE | 18010 |
| MAESTRO | 13672 |
| Wema | 1510 |
| Interswitch | 1227 |
| ACCESS | 373 |
| AMERICAN | 108 |
| DANKORT | 69 |
| VISASTANBIC | 55 |
| DISCOVER | 16 |
