Incident Timeline:
| Date | Event |
|---|---|
| August 21, 2019 | ElasticSearch database discovered. |
| August 21, 2019 | Database owner notified. |
| August 27, 2019 | No response, notified hosting provider. |
| September 3, 2019 | No response, but database secured |
Summary:
Glynk is an Android app with more than 1 million installs. According to their own description: "The Glynk application builds a like-minded network for every user based on interests, opinions, location among many other parameters."
Glynk has also been leaking 2.2 billion rows of data which is roughly 700GB of data. This data has been leaking from another exposed ElasticSearch database that does not have any authentication in place. This database was discovered via Shodan.
Of note: I have not received any word from Glynk following multiple emails, nor did I receive a reply back from the hosting provider after I requested their assistance in notifying their customer and/or blocking access to the exposed database.
How much data?

What was exposed?
For several months (based on the database table names) Glynk has been leaking their user's email address address, username, and the IP the user was accessing the app from.
Usernames and email addresses:
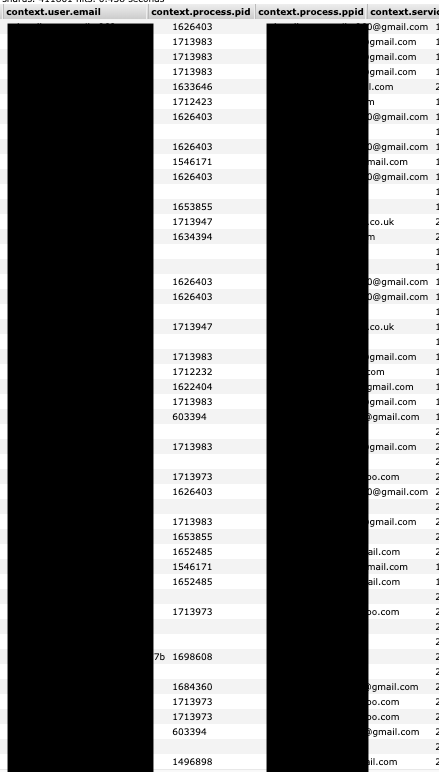
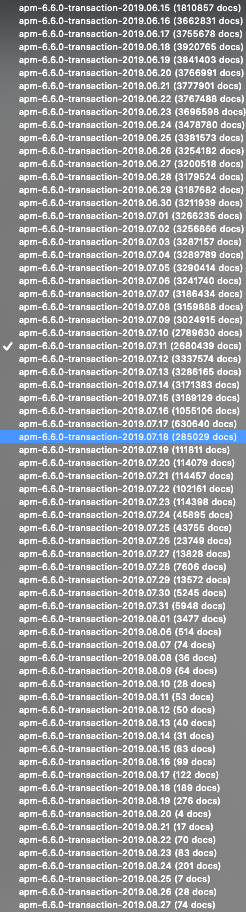
Based on the database tables you'll note this data has been stored (and therefore leaked) going back to at least June 15, 2019. Each database table has several million rows of database containing usernames and emails addresses:
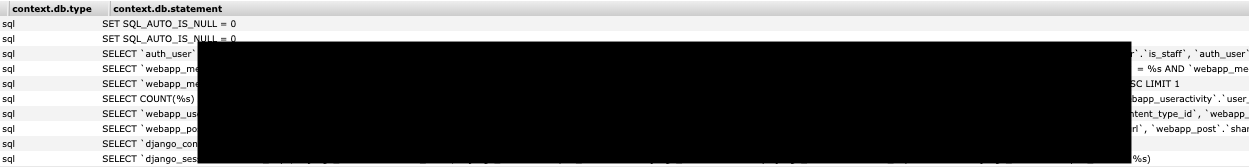
Additionally, the exposed database was also leaking raw production SQL statements. It's important to note that I did not observe any INSERT statements that could have directly exposed customer data. It is generally considered a very bad idea to leak SQL statements though as at the very least it would provide useful information to an attacker as they could easily map out the structure of your database.