Real-time location information leaked by 27 Indian government agencies

Summary
Recently I discovered an improperly secured ElasticSearch server, Kibana server, and InfluxDB administrative page that was associated with a significant amount of data. After investigating the type of content contained on this server it became apparent this was data related to a number of bus and rail agencies within India. The server in question was tracking roughly 11k unique buses (or trains) across India. Follow assistance from India's CERT team the server was properly secured roughly 21 days after it was discovered. I would like to thank India's CERT team for their assistance in securing this server.
Incident Timeline:
| Date | Event |
|---|---|
| November 30, 2018 | Open ElasticSearch server, Kibana web interface, and InfluxDB admin page discovered. |
| December 5, 2018 | I observed the Kibana web interface had been moved behind authentication, but the ElasticSearch server remained publicly accessible. |
| December 5, 2018 | Email sent to India's CERT team to report that the ElasticSearch server and InfluxDB admin page remained exposed. |
| December 5, 2018 | Reply received from CERT team acknowledging the report, but they did not provide a reference number. |
| December 7, 2018 | Issue appeared to be resolved -- the server appeared to be secured. I indicated that I'd like to write about this report. No reply was received. |
| December 16, 2018 | I observed the ElasticSearch server, Kibana web interface, and InfluxDB admin page were again publicly accessible. |
| December 16, 2018 | Follow up email sent to India's CERT team to report that the server was no longer secured. |
| December 21, 2018 | Asked a contact for assistance with resolving this issue. |
| December 22, 2018 | CERT team confirmed the server (ElasticSearch, Kibana, and InfluxDB) had been secured. |
What was found:
A server running ElasticSearch, Kibana, and InfluxDB, and other services was discovered. This server was improperly secured, and authentication was not enabled for these 3 services. As such, a great deal of information was readily available to anyone who connected to the server in question on the correct port number.
The open ElasticSearch server:
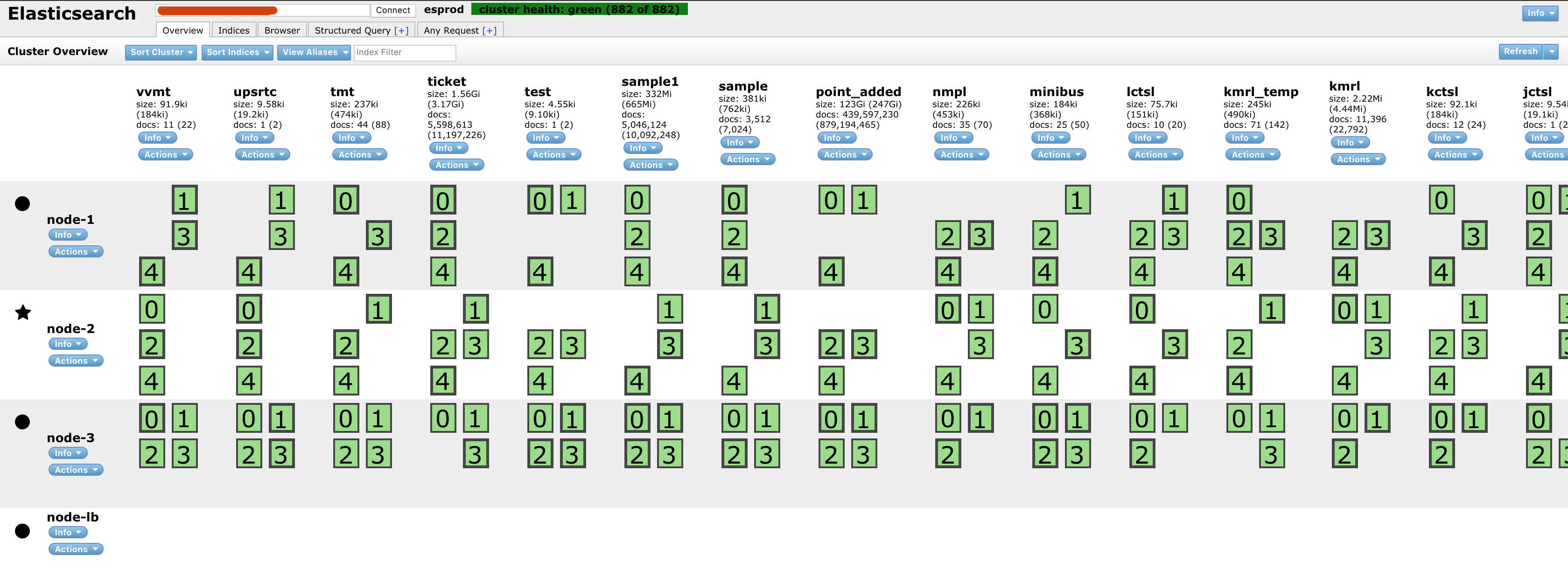
Multiple indices were publicly accessible. These indices correspond to what are effectively different data sets. The count of documents per index varied significantly – ranging from 0 documents to 424 million documents.
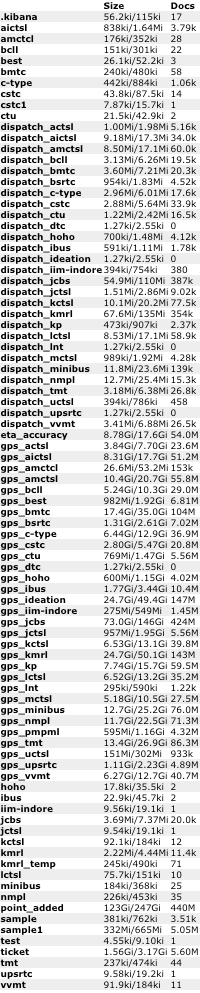
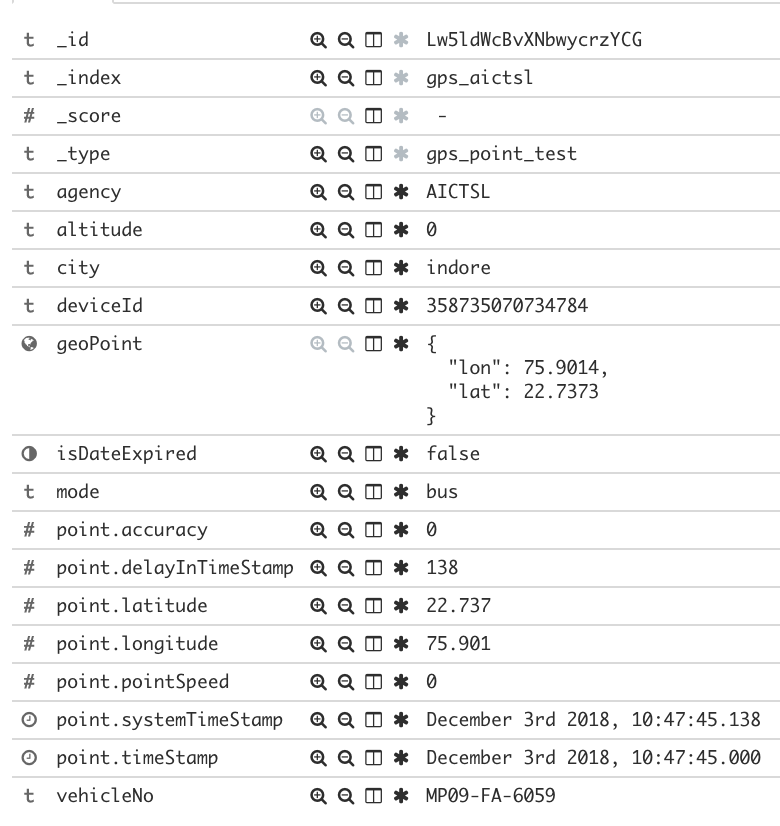
The gps_ indices contained real time GPS information for a variety of agencies (more on that below). This appeared to be the near real time location of various buses (or trains) throughout India.
This GPS information could then be easily mapped to show the location of the roughly 11k unique buses being tracked by this ElasticSearch server (red dots equal more data points):
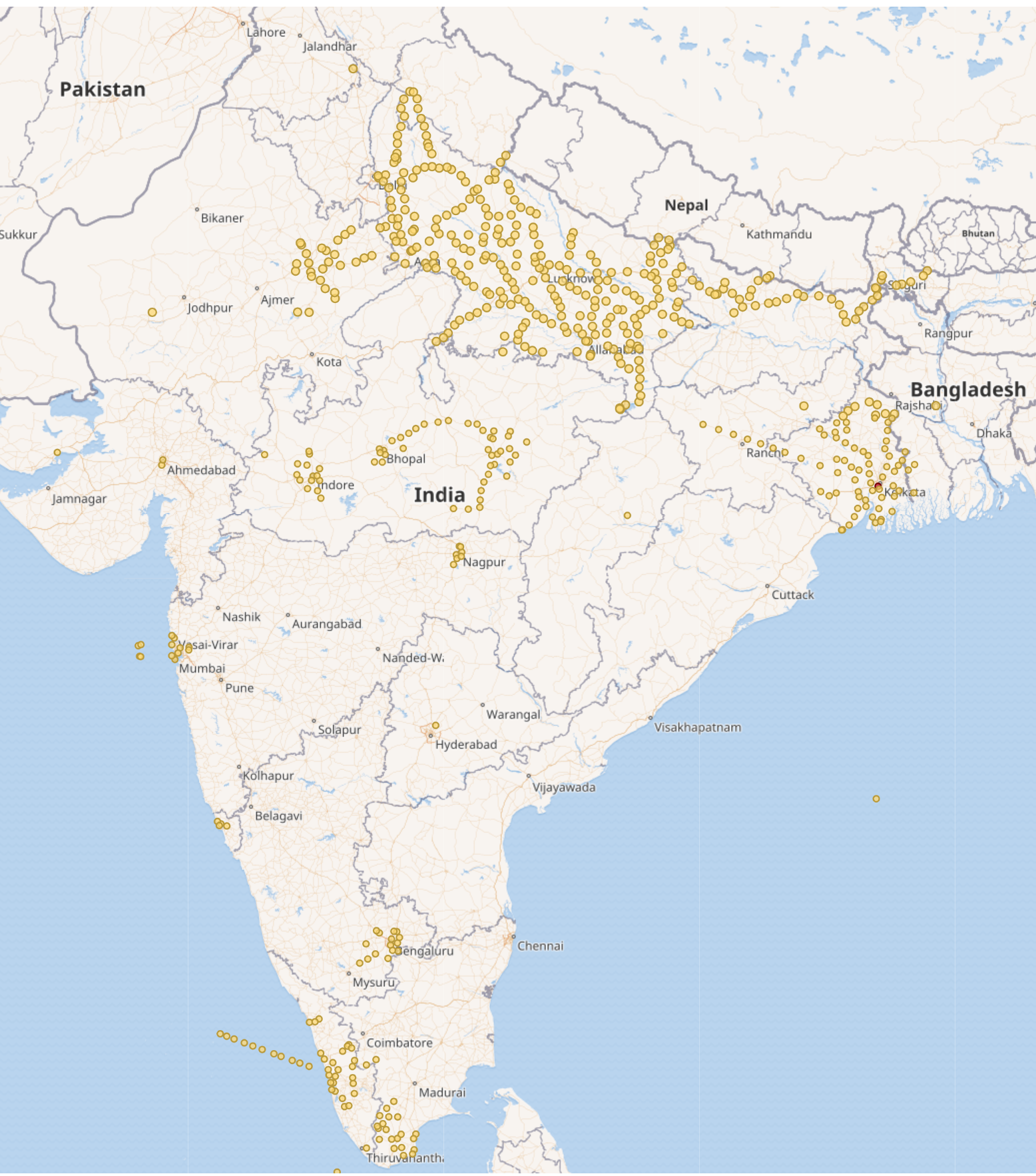
The breakdown of these GPS data points by agency shows the following pattern over a 24 hour period of time:
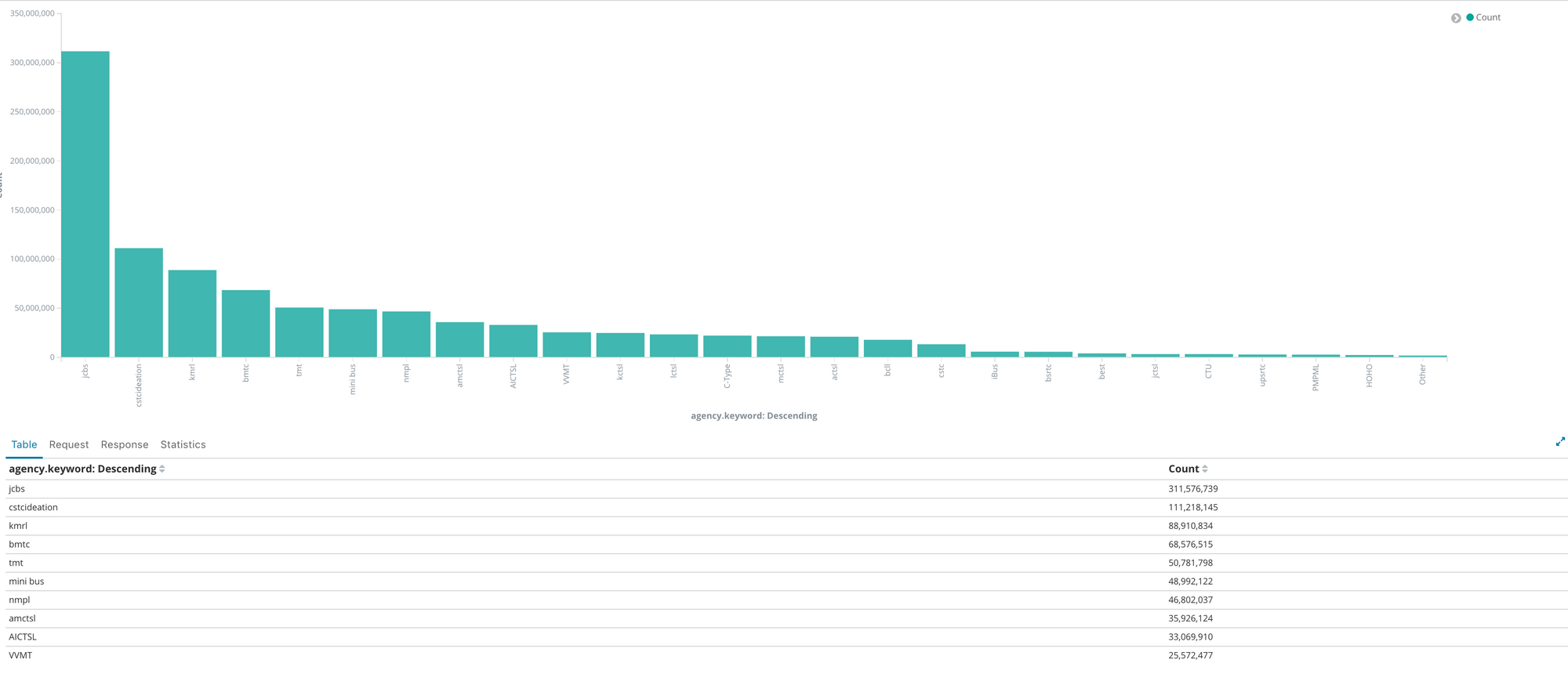
The highest volume of GPS data points (by a lot) comes from Joint Council of Bus Syndicate (JCBS), which is one of the largest public transport bus unions of West Bengal.
The dispatch_ indices contained what appeared to be information regarding riders of buses (or trains in the case of KMRL) using those various agencies.
Who are these agencies?
| Acronym | Agency | Interested info |
|---|---|---|
| ACTSL | Allahabad City Transport Services Limited | -- http://uputd.gov.in/allahabadctsl |
| AICTSL | Atal Indore City Transport Services Limited | -- http://citybusindore.com/ -- http://aictslportal.infinium.management/ListofRoutes/ViewRoutes |
| AMCTSL | Agra-Mathura City Transport Services Limited | -- http://amctsl.org -- http://uputd.gov.in/agractsl |
| BCLL | Bhopal City Link Limited | -- http://mybusbhopal.in/ |
| BMTC | Bangalore Metropolitan Transport Corporation | -- http://www.mybmtc.com/ |
| BSRTC | Bihar State Road Transport Corporation | -- http://bsrtc.org.in/ |
| C-TYPE | Could not locate anything conclusive | |
| CSTC | Calcutta State Transport Corporation | -- https://en.wikipedia.org/wiki/Calcutta_State_Transport_Corporation |
| CTU | Chandigarh Transport Undertaking | -- http://chdctu.gov.in/ |
| DTC | Delhi Transport Corporation | -- https://en.wikipedia.org/wiki/Delhi_Transport_Corporation |
| HOHO | Hop On Hop Off Sightseeing Bus Service, Govt. of Delhi | -- http://hohodelhi.com/ |
| IBUS | Indore Bus Rapid Transit System | -- https://en.wikipedia.org/wiki/Indore_Bus_Rapid_Transit_System |
| JCBS | Joint Council of Bus Syndicate | |
| JCTSL | Jaipur City Transport Services Limited | -- https://en.wikipedia.org/wiki/Jaipur_City_Transport_Services_Limited |
| KCTSL | Kanpur City Transport Services Limited | -- https://en.wikipedia.org/wiki/Kanpur_City_Transport_Services_Limited -- http://uputd.gov.in/kanpurctsl |
| KMRL | Kochi Metro Rail Limited | -- http://www.kochimetro.org/ |
| KP | Could not locate anything conclusive | |
| LCTSL | Lucknow City Transport Services Limited | -- http://lctsl.org/ |
| LNT | Lukshmi Narayan Travels | |
| MCTSL | Meerut City Transport Services Limited | -- http://mctsl.org/FareRules.aspx |
| MINIBUS | Could not locate anything conclusive | |
| NMPL | Nagpur Mahanagar Parivahan Limited | -- https://en.wikipedia.org/wiki/Nagpur_Mahanagar_Parivahan_Limited |
| TMT | Thane Municipal Transport | -- https://en.wikipedia.org/wiki/Thane_Municipal_Transport -- https://thanecity.gov.in/department_details.php?id=34 |
| UCTSL | Ujjain City Transport Services Limited | |
| UPSRTC | Uttar Pradesh State Road Transport Corporation | -- http://www.upsrtc.com/ -- "UPSRTC carries over 523 million passengers annually" |
| VVMT | Vasai Virar Municipal Transport | -- https://en.wikipedia.org/wiki/Vasai-Virar_City_Municipal_Corporation -- http://vvcmc.in/vvmc/?page_id=523&lang=en |
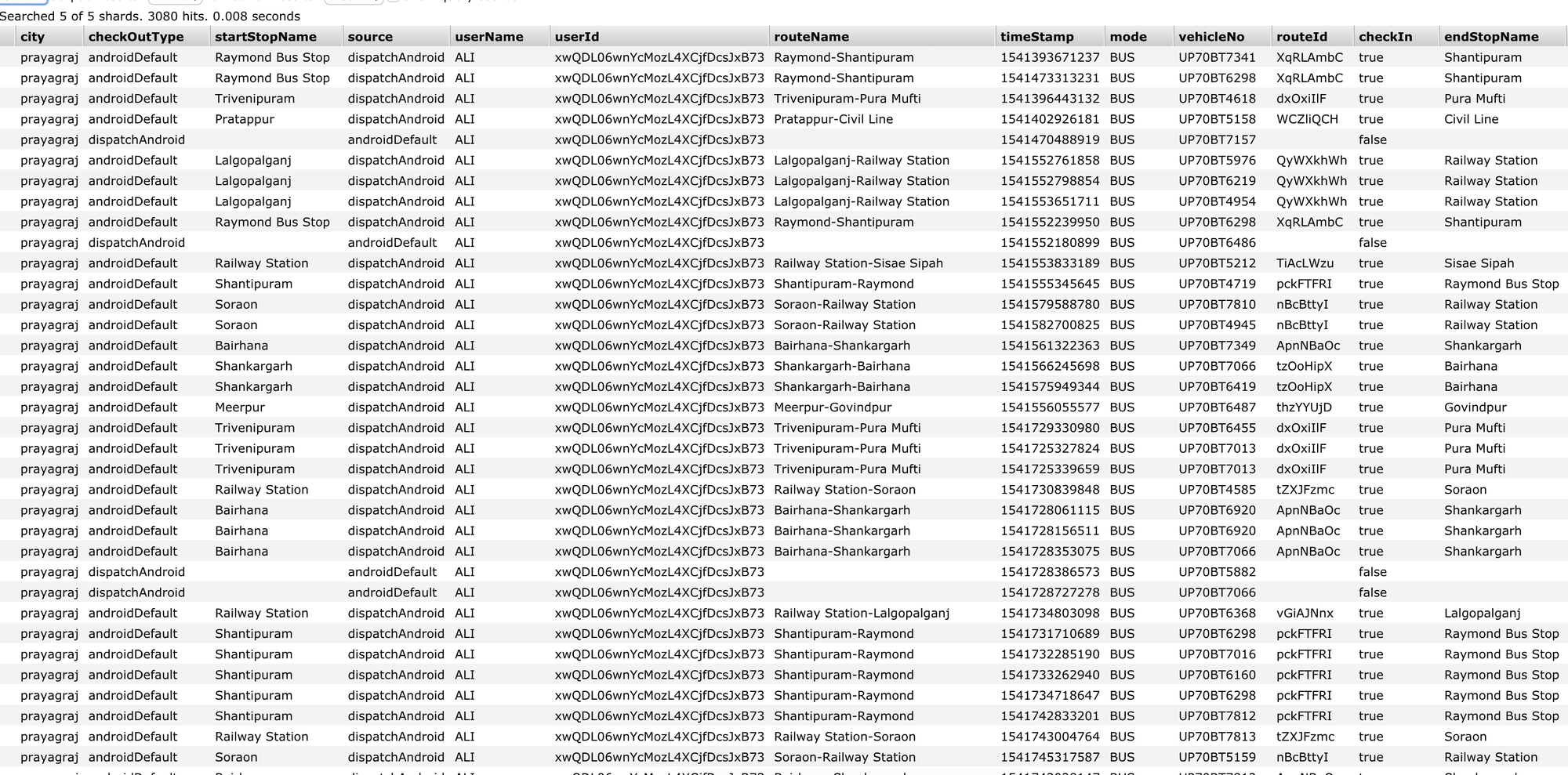
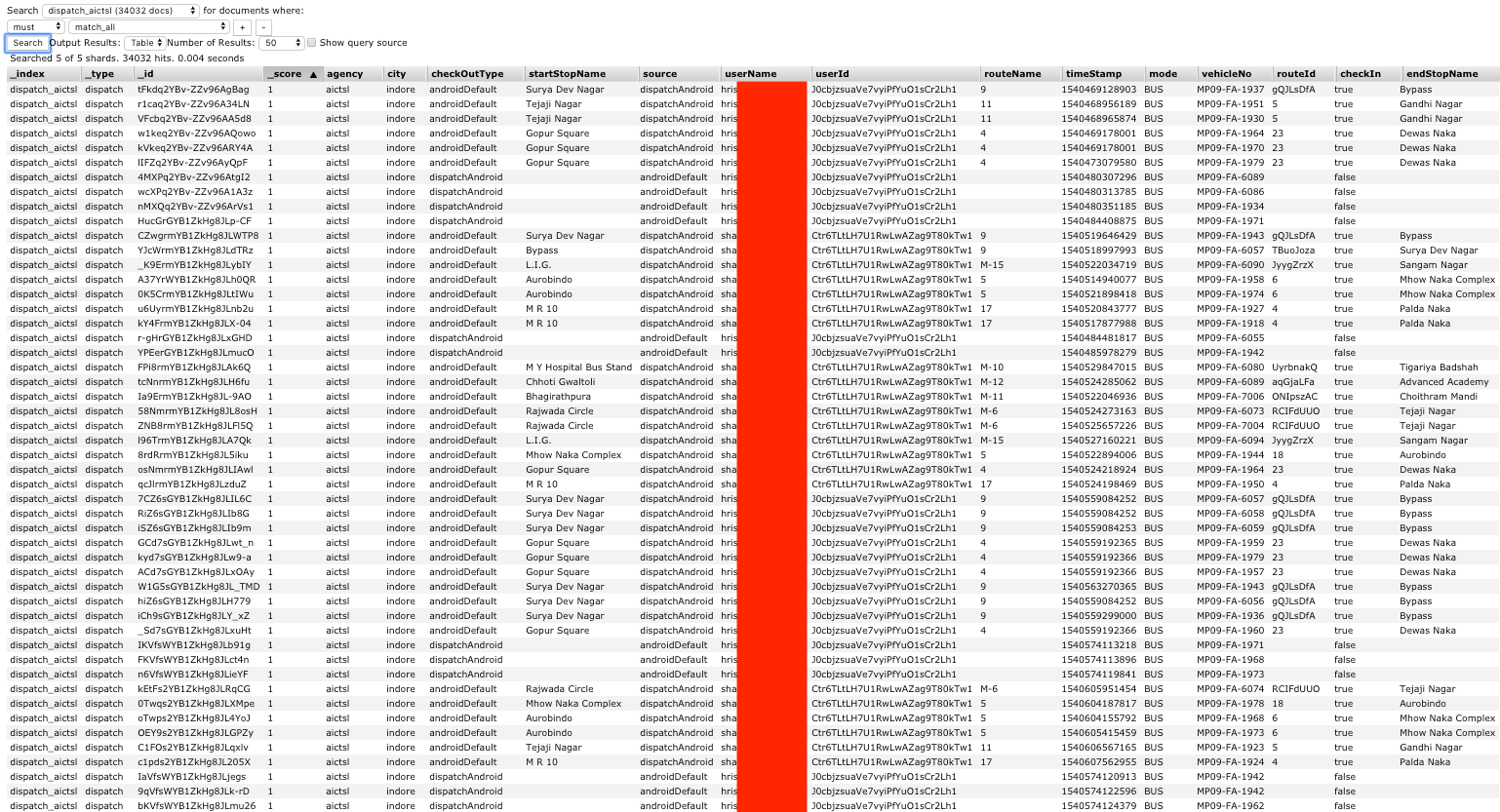
In some cases the username value used by the agency appeared to be the rider's full name:
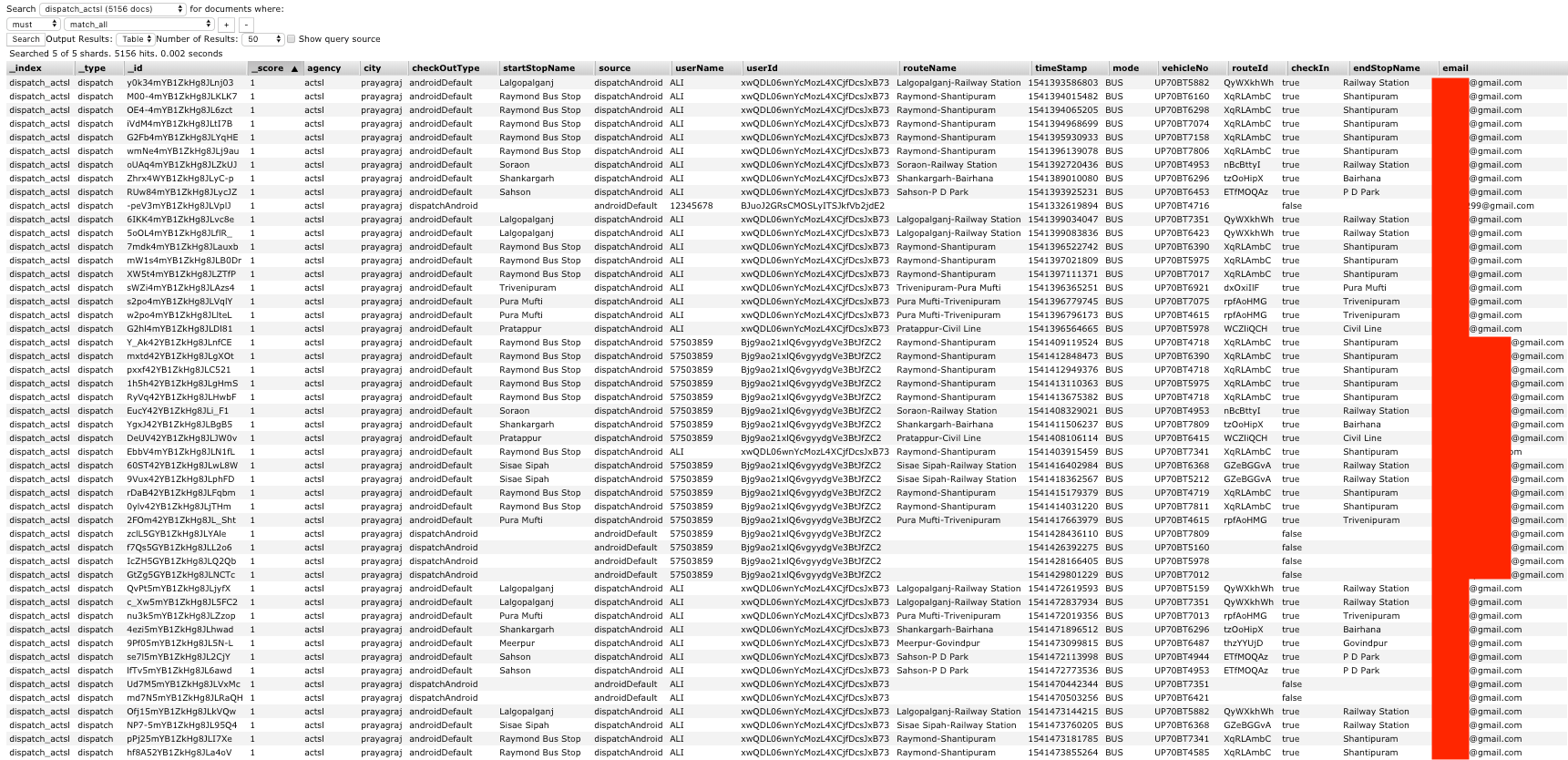
For some other agencies it appears the username seemed to be user-configured value, but in those cases the user's email address was also exposed:
Baseds on the userId or the email address value it would be possible to get a reasonable idea of where an individual rider had traveled, and when: