Web of Tech Support Scam Domains

TL;DR: at least 2,102 tech support scam (TSS) domains.
Initial domain I came across: hXXp://ghryuiefdao{.}tk/?number=888-348-1742&bluer=1
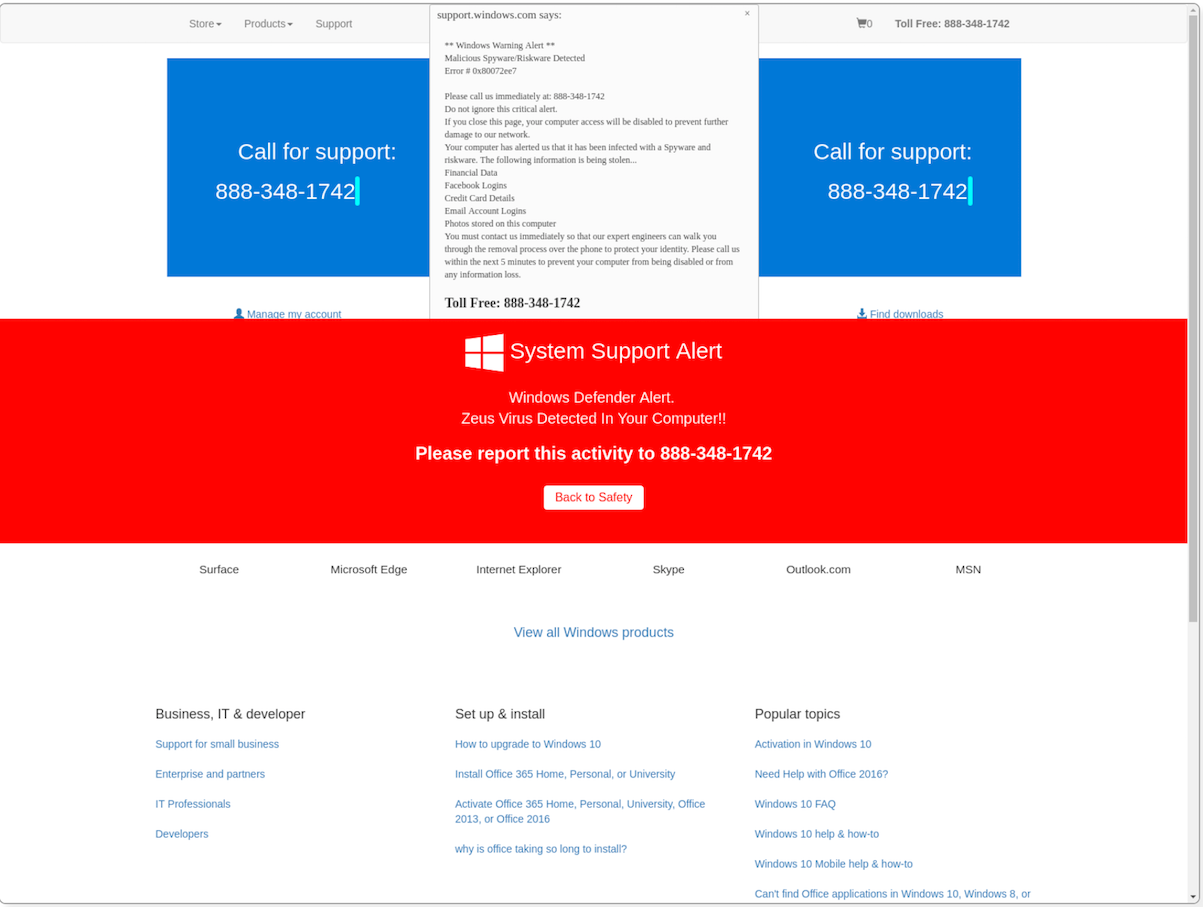
2018-07-22 UPDATE:
Freenom (the registrar) killed all of the 2,075 .tk domains.
dig ghryuiefdao.tk | grep "status"
;; ->>HEADER<<- opcode: QUERY, status: NXDOMAIN, id: 254862018-07-18 UPDATE:
Total Server Solutions has terminated service.
New host is Virtual Machine Solutions.
;; ANSWER SECTION:
ghryuiefdao{.}tk. 56 IN A 107.174.221.209https://whois.ext.cftools.net/get/107.174.221.209 --> Virtual Machine Solutions (virmach{.}com)
2018-07-07 UPDATE:
Leaseweb has terminated service.
New host is Total Server Solutions
;; ANSWER SECTION:
ghryuiefdao{.}tk. 60 IN A 107.181.160.18https://whois.ext.cftools.net/get/107.181.160.18 --> Total Server Solutions (totalserversolutions{.}com)
OLD HOST before 2018-07-07:
;; ANSWER SECTION:
ghryuiefdao{.}tk. 36 IN A 172.241.166.101https://whois.ext.cftools.net/get/172.241.166.101 --> Leaseweb
https://my.farsightsecurity.com/dnsdbui/ --> pivot off 172.241.166.101
Returned 3167 RRsets
List of domains (courtesy of Farsight's DNSdb):
Suspect Domains
Downloaded the DNSdb results as a JSON file. Removed obvious subdomains such as "www" to remove most of the duplicates. --> sed -i '' '/www/d' domains.json
ccTLD/TLD breakdown:
2,075 tk
172 com
22 bid
3 review
2 win
1 webcam
1 streamCheck if all these domains also trigger the same scareware page -- specifically find and output the phone # the scareware message references.
for i in $(cat domains.json | jq -r .rrname); do echo $i; curl -s "http://$i/?number=888-348-1742&bluer=1" | grep "text_short" | awk -F ":" '{print $3}'; done > out.txt
Here's the output file: output
This check will generate 3 lines per domain in this format:
alsayerkw{.}webcam.
888-348-1742 (Toll Free)";
##blank line here##Get the line numbers: cat out.txt | wc -l and then divide by 3. It's not perfect obviously, but 2,102.6 domains out of the original 3,167 from the DNSdb file.
Random observation: The i.php file seems to be returning the current time.
curl -s "hXXp://ghryuiefdao{.}tk/i.php"
1530680348
curl -s "hXXp://ghryuiefdao{.}tk/i.php"
1530680350
curl -s "hXXp://ghryuiefdao{.}tk/i.php"
1530680351
curl -s "hXXp://ghryuiefdao{.}tk/i.php"
1530680352
curl -s "hXXp://ghryuiefdao{.}tk/i.php"
1530680353Off to Leaseweb to get the origin server burned down, and then to Freenom to burn down the domains.